In today’s cybersecurity landscape, thick client applications—software that runs on local machines while interacting with remote servers—must be equipped with robust security measures to defend against a variety of attacks. To strengthen security and reduce the likelihood of exploitation, modern software often integrates several mitigation techniques during the build process. These features, designed to make it more difficult for attackers to exploit vulnerabilities, play a crucial role in protecting thick client applications. This article explores seven key security mitigations employed for thick client applications.
Therefore, to identify vulnerabilities or misconfigurations that could be exploited by attackers to gain unauthorized access or disrupt the TOE services, the evaluator can use tools like PE Security (refer to Test tools validation form) to check if a Windows binary (EXE/DLL) has been compiled with ASLR, DEP, SafeSEH, StrongNaming, Authenticode, Control Flow Guard, and HighEntropyVA.By default, all points should be set to TRUE. However, if DotNET is TRUE, SafeSEH should also be set to TRUE.
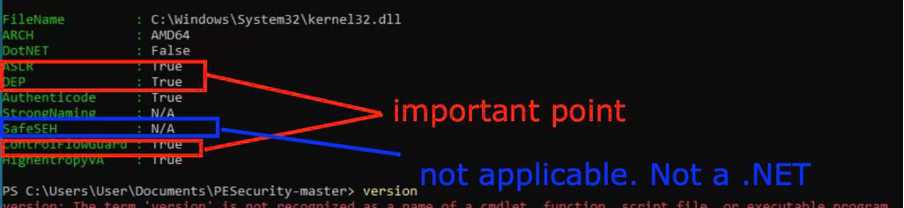
1. ASLR (Address Space Layout Randomization)
ASLR is a critical security feature that enhances the protection of thick client applications by randomizing the memory addresses used by system and application processes. Without ASLR, memory locations for executable code and data structures are predictable, making it easier for attackers to guess and exploit vulnerabilities like buffer overflows. By introducing randomness into memory address allocation, ASLR significantly complicates attempts to carry out memory corruption attacks.
In the context of thick clients, ASLR ensures that each time the application runs, the memory addresses for key components are different, reducing the predictability required for successful exploitation.
2. DEP (Data Execution Prevention)
DEP is a security mitigation designed to prevent certain types of exploits that involve executing malicious code from memory regions that are intended to store only data, such as the heap or stack. DEP enforces a policy that marks memory regions as non-executable, ensuring that even if an attacker injects code into these regions, it cannot be executed.
In thick client applications, DEP helps mitigate attacks like buffer overflows by preventing executable payloads from running in protected memory areas. This adds another layer of protection, especially when combined with ASLR.
3. SafeSEH (Safe Structured Exception Handling)
SafeSEH is a security feature that safeguards against exploits targeting structured exception handling (SEH) in Windows applications. SEH is a mechanism that allows software to gracefully handle unexpected conditions or errors. However, attackers have been known to exploit SEH as a vector to hijack the execution flow of applications.
SafeSEH mitigates this risk by maintaining a list of legitimate exception handlers that are compiled into the application. If an attacker attempts to introduce a malicious handler, SafeSEH will detect it and prevent it from executing. This feature is particularly useful in preventing attacks that exploit vulnerabilities related to memory corruption or buffer overflows in thick client applications.
4. Strong Naming
For .NET-based thick client applications, Strong Naming is an essential security feature that ensures the integrity and authenticity of the application’s assemblies. When an assembly is strong-named, it is assigned a unique identity that includes the assembly’s name, version number, culture information, and a public key. This prevents attackers from tampering with or substituting assemblies without being detected.
Strong naming verifies that the assemblies used by the application have not been altered or replaced, ensuring that only trusted and authenticated components are loaded. This prevents potential attacks where malicious code could be injected into the application by substituting one of its assemblies.
5. Authenticode
Authenticode is a Microsoft technology used to digitally sign executables and DLLs, allowing the operating system and users to verify the identity of the software publisher. The digital signature ensures that the code has not been altered since it was signed, offering assurance that the software comes from a trusted source.
For thick client applications, Authenticode prevents tampered or unauthorized code from running on users’ machines. It is particularly useful in environments where software is distributed and installed locally, as it helps users avoid running untrusted software that could introduce malware or other security risks.
6. Control Flow Guard (CFG)
Control Flow Guard (CFG) is a mitigation technique designed to protect against control flow hijacking attacks, such as Return-Oriented Programming (ROP). In these attacks, an adversary takes control of the execution flow of a program by manipulating the application’s memory to jump to unintended code sequences.
CFG works by creating a map of valid indirect calls within the application and ensuring that only valid control flow transfers are allowed. If an attacker attempts to redirect the control flow to an unintended or malicious location, CFG will detect and block the action. In thick client applications, CFG provides a critical defense against advanced memory corruption attacks that attempt to hijack control flow.
7. High Entropy VA
High Entropy Virtual Addressing (VA) is an enhancement to ASLR that further increases the randomness of memory address allocation, especially for 64-bit applications. By increasing the available address space and adding more entropy (randomness) to the virtual address layout, High Entropy VA makes it even more difficult for attackers to predict the location of executable code or data.
In thick client applications, High Entropy VA is especially valuable for 64-bit versions, as it helps to enhance ASLR’s effectiveness by further reducing the predictability of memory locations. This mitigates the risk of memory corruption exploits and ensures a higher level of security for locally running applications.
Conclusion
Thick client applications are often an essential part of enterprise systems, but their local execution and interaction with backend systems make them an attractive target for attackers. To mitigate potential security risks, modern software builds incorporate several key security features like ASLR, DEP, SafeSEH, Strong Naming, Authenticode, Control Flow Guard, and High Entropy VA.These security mitigations work together to prevent exploitation and make it significantly harder for attackers to exploit vulnerabilities in thick client applications. By integrating these defenses into the application’s build process, developers can help ensure that thick client software remains resilient against common exploitation techniques, providing a more secure experience for users and enterprises alike.
Prepared by: Nur Sharifah Idayu Mat Roh