In the ever-evolving landscape of mobile applications, the safety and security of user data is paramount. Mobile app security testing is not just a precaution; it’s a necessity to protect your users and uphold their trust. Welcome to this comprehensive walkthrough, where we will guide you through the intricacies of mobile app security testing using MobSF (Mobile Security Framework).
Our goal in this walkthrough is to provide you with a clear and practical path to effectively secure your mobile applications. This guide is your trusted companion on the journey to understanding and implementing security testing.
Tool Installation
Reference: https://mobsf.github.io/docs/#/mobsf_docker?id=download
1. Ensure docker installed to run MobSF.
2. Open terminal and enter command.
# docker pull opensecurity/mobile-security-framework-mobsf:latest
3. Ensure any of the supported Genymotion Android VM/ Android Studio Emulator before running MobSF
4. Create an Android Virtual Device (AVD) without Google Play Store follow requirement of Supports arm, arm64, x86 and x86_64 architecture Android 5.0 – 9.0, upto API 28.
5. Open terminal and append your Android SDK emulator directory to PATH environment variable. Navigate to C:\Users\<user>\AppData\Local\Android\Sdk\emulator
6. Enter below command to list emulators.
# emulator -list-avds
7. Enter command and insert <non_production_avd_name> to emulator chosen
# emulator -avd <non_production_avd_name> -writable-system -no-snapshot Emulator will start running.
8. Emulator will start running.
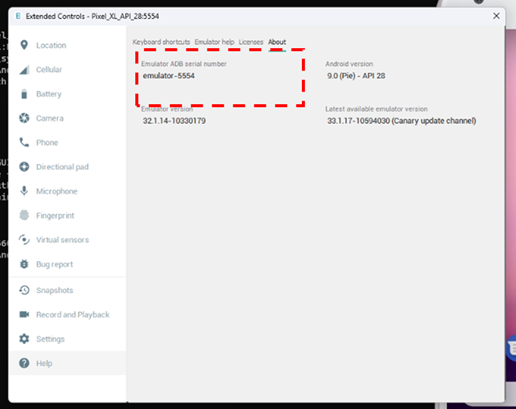
9. Identify the emulator serial number.
10. Start docker application
11. Enter below command and insert the adb device identifier with the emulator serial number
# docker run -it –rm -p 8000:8000 -p 1337:1337 -e MOBSF_ANALYZER_IDENTIFIER=<adb device identifier> opensecurity/mobile-security-framework-mobsf:latest
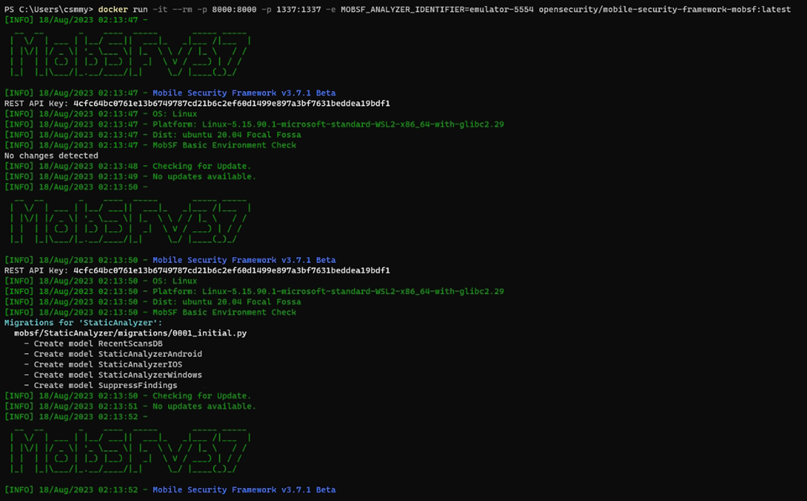
12. Browsing http://localhost:8000/
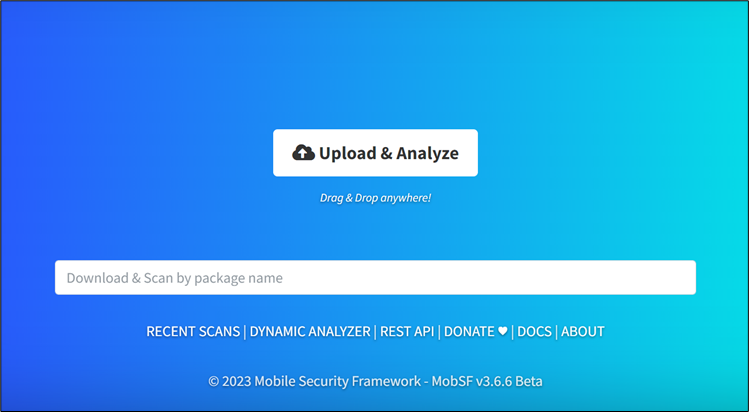
Mobile application static analysis (Manifest Analysis)
1. Browsing http://localhost:8000/
2. Click on Upload & Analyze
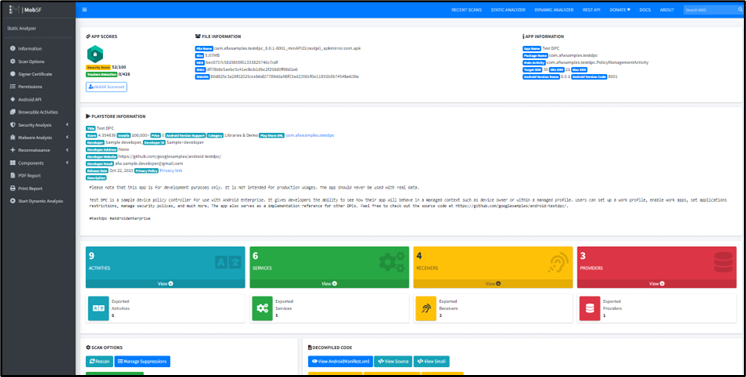
3. Waiting the application being analysed
4. After analysis completed, report of static analysis will be viewed.
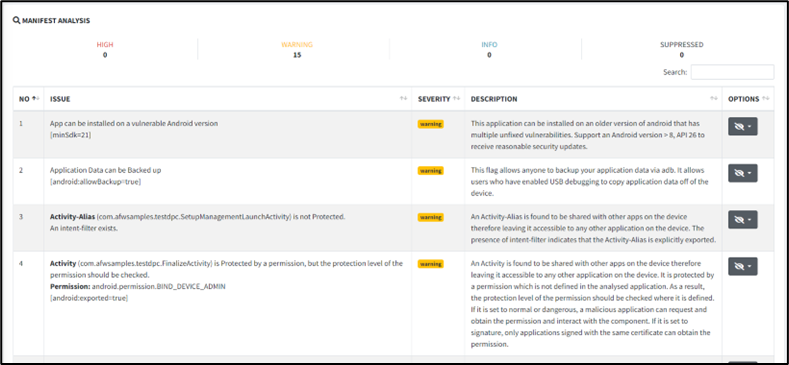
5. To view manifest analysis, on the sidebar menu, choose Security Analysis and click on Manifest Analysis.
6. The report will navigate to the manifest analysis section. The report allows us to identify any vulnerabilities within the AndroidManifest.xml file, including a detailed description of the permissions analysis. Through MobSF’s analysis of the application’s permissions and their associated risks, including any potential misuse of those permissions. It also provides analysis of the app’s activities, services, and receivers. The analysis also includes a detailed description of the exported components and the intent filters they use.
Mobile application dynamic analysis.
1. At sidebar menu, choose Scan Options
2. Click on Start Dynamic Analysis.
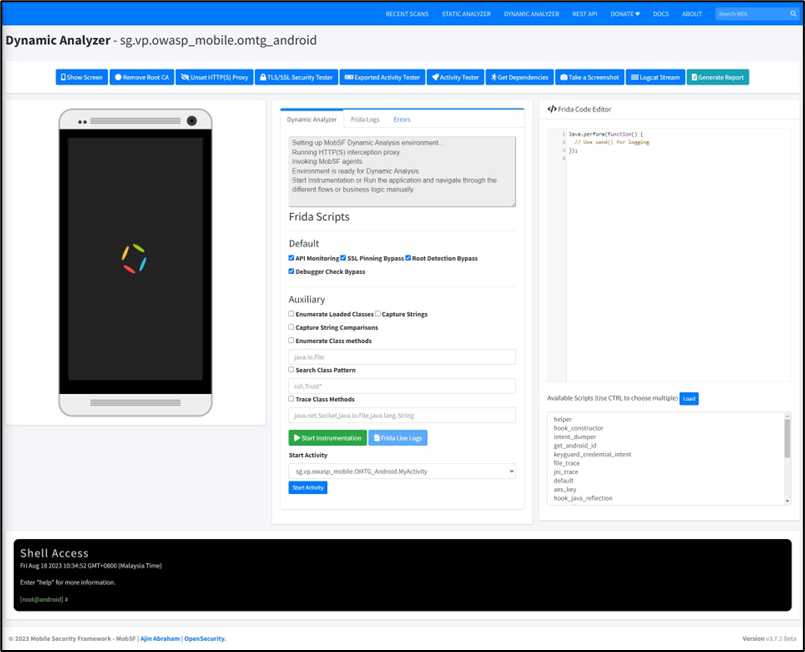
3. After dynamic analysis have been done. Click on Generate Report to view the report of the analysis.
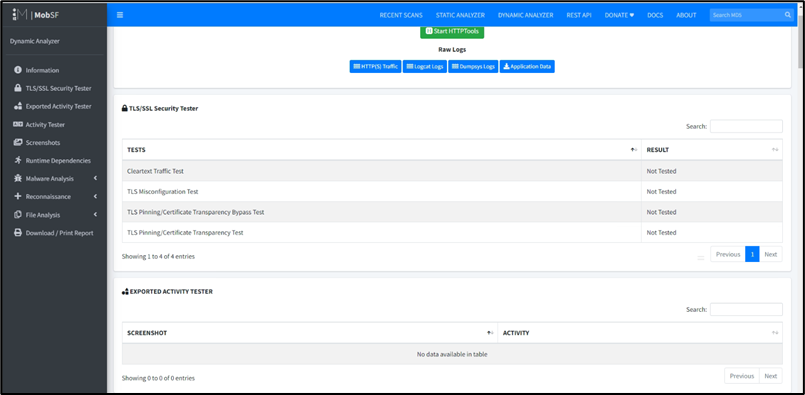
Mobile malware analysis.
1. To view malware analysis, on the sidebar menu, click on Malware Analysis.
2. Click on APKiD Analysis
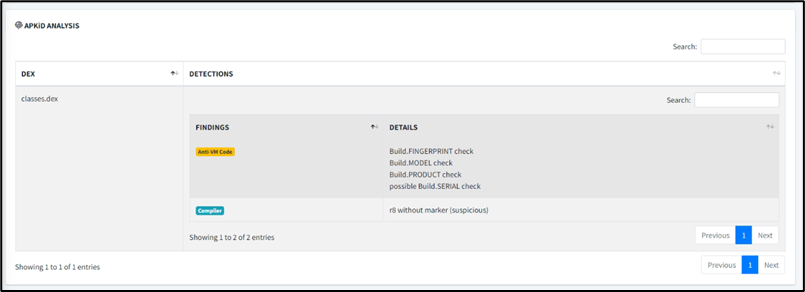
3. Click on Quark Analysis
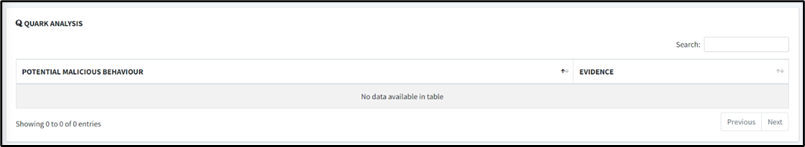
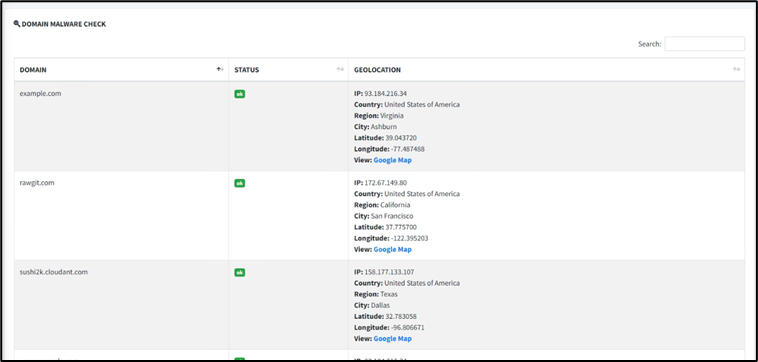
4. Click on Server Locations
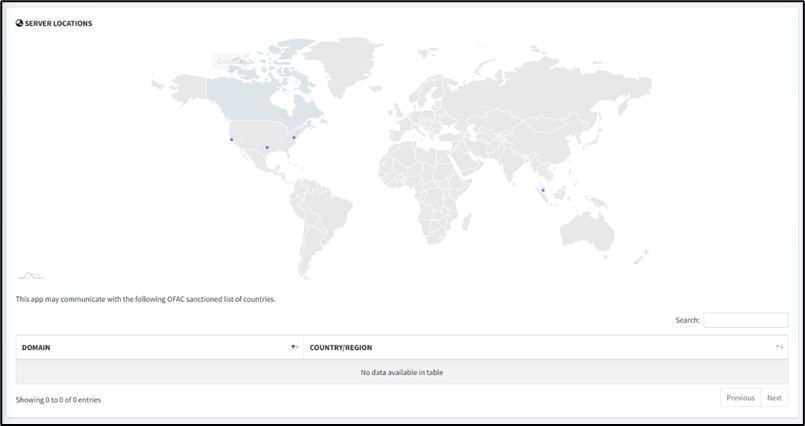
5. Click on Domain Malware Check